🛡️Information System Audits (IS)
In today’s digital age, businesses rely on technology to drive efficiency and innovation. At RKCO East Africa Consulting, we provide comprehensive IS Audits to assess the security, integrity, and efficiency of your IT infrastructure.
An Information System (IS) Audit is a comprehensive examination and evaluation of an organization’s information systems, management controls, and related operations. The goal is to ensure data integrity, security, efficiency, and compliance with relevant policies and regulations.
Our audits help identify vulnerabilities, ensure compliance with industry regulations, and optimize system performance, giving you confidence in your technology investments.
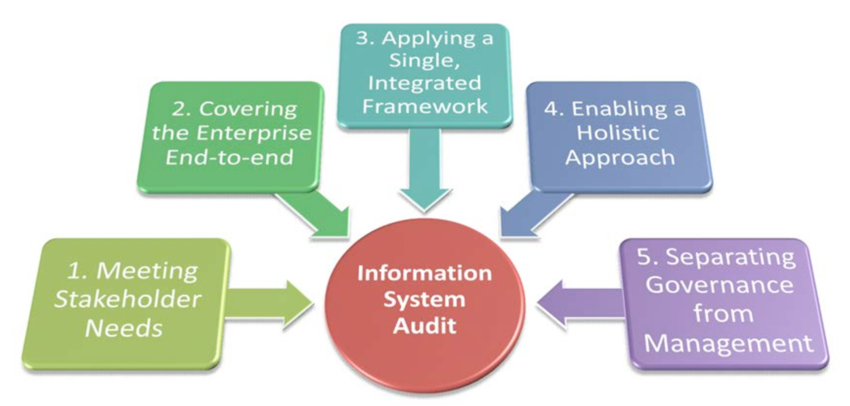
Our (IS) Audits Cover but not limited to:
IT General Controls
These are broad policies and procedures that apply to all areas of the IT environment:
1. IT governance and management
2. Access controls (physical and logical)
3. Change management procedures
4. Backup and disaster recovery plans
5. Incident response mechanisms
6. Vendor and third-party management
1. IT governance and management
2. Access controls (physical and logical)
3. Change management procedures
4. Backup and disaster recovery plans
5. Incident response mechanisms
6. Vendor and third-party management
Application Controls
These are controls specific to individual software applications, ensuring data accuracy and processing integrity:
1. Input, processing, and output controls
2. Data validation and error handling
3. Authorization procedures
4. Audit trails
1. Input, processing, and output controls
2. Data validation and error handling
3. Authorization procedures
4. Audit trails
Security Controls
1. Network security (firewalls, intrusion detection/prevention)
2. Endpoint security (antivirus, patch management)
3. User access management (roles, permissions, authentication)
4. Encryption and secure communication protocols
2. Endpoint security (antivirus, patch management)
3. User access management (roles, permissions, authentication)
4. Encryption and secure communication protocols
Data Integrity and Confidentiality
1. Protection of data from unauthorized access or alterations
2. Compliance with data protection regulations (e.g., GDPR, HIPAA)
3. Data classification and retention policies
2. Compliance with data protection regulations (e.g., GDPR, HIPAA)
3. Data classification and retention policies
IT Operations
1. System performance and availability
2. Capacity planning and resource utilization
3. Monitoring of system logs and alerts
2. Capacity planning and resource utilization
3. Monitoring of system logs and alerts
Compliance
1. Adherence to internal policies, procedures, and standards
2. Regulatory compliance (e.g., SOX, PCI-DSS)
3. Industry best practices (e.g., COBIT, ISO/IEC 27001)
2. Regulatory compliance (e.g., SOX, PCI-DSS)
3. Industry best practices (e.g., COBIT, ISO/IEC 27001)
Business Continuity and Disaster Recovery
1. Evaluation of backup systems
2. Recovery time and recovery point objectives (RTO & RPO)
3. Regular testing of DR plans
2. Recovery time and recovery point objectives (RTO & RPO)
3. Regular testing of DR plans
Project Management and System Development
1. Review of IT project lifecycle (planning, development, testing, deployment)
2. Risk assessments during project phases
3. Change control processes
2. Risk assessments during project phases
3. Change control processes
We Audit. You Advance.
Our (IS) Information System Audit services reveal hidden risks, improve control systems, and ensure IT compliance—so your business can operate with confidence in an increasingly digital world.
Talk to us Today



